Citizen Lab destroys spyware

We are big fans (and small supporters) of Canada's Citizen Lab in Toronto, as part of our Internet Security advice for persons of interest.
CitizenLab is perhaps most famous for their end to end investigation of NSO group's Pegasus spyware – originally found in a Human Rights Foundation activist's phone – Tracking it all the way back to Saudi servers as depicted in the award winning film The Dissident – and later leading to block buster stories that roiled politics in numerous countries – to ultimately lawsuits by Apple and Meta that bankrupted private equity backed Israeli company NSO.
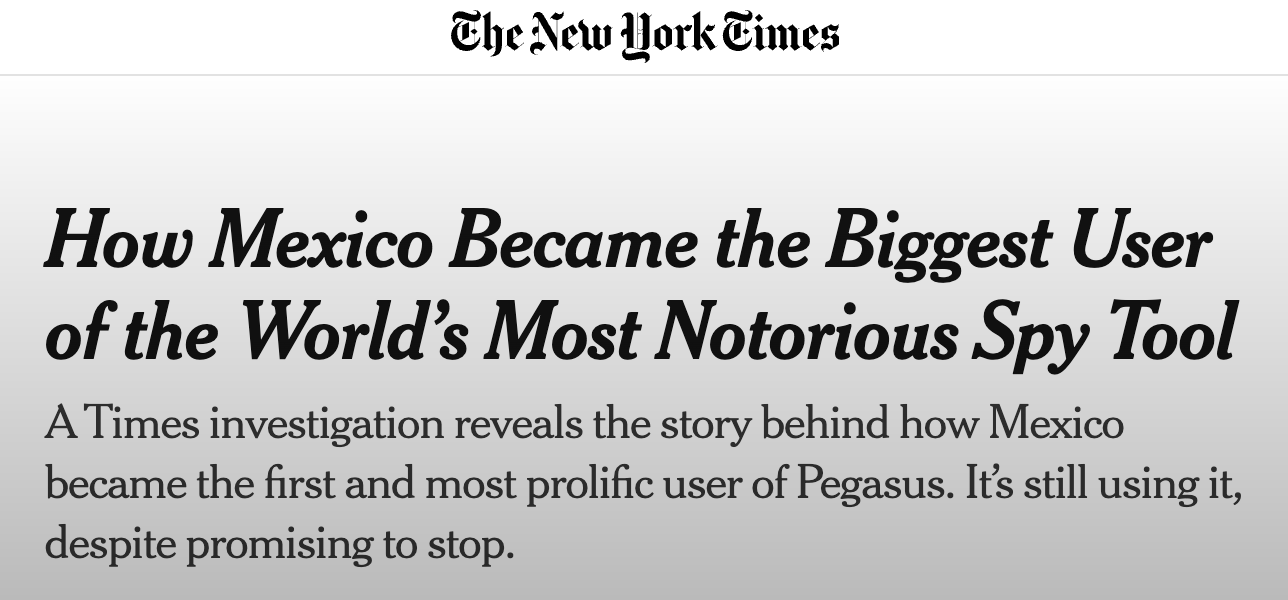
NSO had claimed they were selling the software only to catch terrorists in limited rgions, but Citizen Lab's work demonstrated NSO was blatantly lying time and time again and it had been used for purposes as mundane as surveiling Mexican citizens who were lobbying for a cartel opposed soft drink tax... and as brash as spying on heads of state - leading NSO to be sanctioned by the US.
Not just any heads of state – major political leaders all over the world. Pegasus was misused by or targeted towards Armenia, Azerbaijan, Bahrain, Djibouti, Dominican Republic, Egypt, El Salvador, Estonia, Finland, France, Germany, Hungry, India, Iraq, Israel, Jordan, Kazakstan, Latvia, Mexico, Morocco, Netherlands, Panama, Palestine, Poland, Rwanda, Saudi Arabia, Slovakia, South Africa, Spain, Thailand, Tibet, Togo, Thailand, Uganda, Ukraine, UAE, UK, US, Yemen,
To get an idea what this looks like in the US see:
https://en.wikipedia.org/wiki/Pegasus_(spyware)
NSO Group pitched its spyware to the Drug Enforcement Administration (DEA), which declined to purchase it due to its high cost.[193]
In August 2016, NSO Group (through its U.S. subsidiary Westbridge) pitched its U.S. version of Pegasus to the San Diego Police Department (SDPD). In the marketing material, Westbridge emphasized that the company is U.S.-based and majority-owned by a U.S. parent company. An SDPD Sergeant responded to the sales pitch with "sounds awesome". The SDPD declined to purchase the spyware as it was too expensive.[40]
In July 2021, it was revealed that the phone numbers of about a dozen U.S. citizens – including diplomats, journalists, aid workers, and dissident expatriates. Among the phone numbers discovered on the list were those of the Obama administration's chief negotiator of the Joint Comprehensive Plan of Action as well as those of several United Nations diplomats residing in the U.S. NSO Group has said that Pegasus is not deployed against any device located within the territory of the U.S., but it has been suggested that U.S. citizens can become targets when abroad.[194]
In December 2021, it was reported that Pegasus spyware was found in the preceding months on the iPhones of at least nine U.S. State Department employees, all of whom were either stationed in Uganda or worked on matters related to Uganda.[195] Later the same month, AP reported that a total of 11 U.S. State Department employees stationed in Uganda had their iPhones hacked with Pegasus.[196] The US government blacklisted the NSO Group to stop what it called "transnational repression".[197]
In January 2022, it was reported that the Federal Bureau of Investigation had secretly bought the Pegasus spyware in 2019 and had seen a demonstration of Phantom, a newer tool capable of targeting American phone numbers. The FBI went on to test both tools, and considered their use for domestic surveillance in the U.S., which reportedly led to discussions between the FBI and United States Department of Justice; ultimately the FBI decided against using NSO spyware. However, despite the 2021 decision rejecting use of NSO software, Pegasus equipment is still in the FBI's possession at a New Jersey facility.[198][199] Responding to the reports, FBI officials played down the domestic surveillance aspect of the Pegasus testing, instead stressing counter-intelligence as their purported main goal. A document later obtained by The New York Times clearly showed that the agency weighed using Pegasus and Phantom in domestic law enforcement cases.[200][201]
L3Harris, a U.S. defense contractor, was in talks to acquire NSO Group, the maker of Pegasus. L3Harris reportedly had the backing of U.S. intelligence in undertaking the acquisition negotiations. After months of negotiations, the talks were scuttled after they were made known to the public by the news media in June 2022, with the U.S. government publicly rebuking the acquisition attempt.[61]
In March 2023, President Joe Biden signed an executive order that prohibited "operational use by the United States Government of commercial spyware that poses risks to national security or has been misused by foreign actors to enable human rights abuses around the world."
In addition to all their amazing work on Pegasus, Citizen Lab has been an incredible ally personally investigating cyber security issues for Good Ancestor's team and grantees we support.
They also contributed to one of the security tools we recommend in our Internet Security advice for persons of interest It has now become Consumer Report's Security planner.
View their publications
Find them on X
See also